Get your mobile applications appraised from an attacker’s perspective to uncover potential security flaws. Ensure maximal data security and build customer trust by remediating exploitable vulnerabilities through corrective insights gleaned from AppSecure’s meticulous offensive mobile app penetration testing.
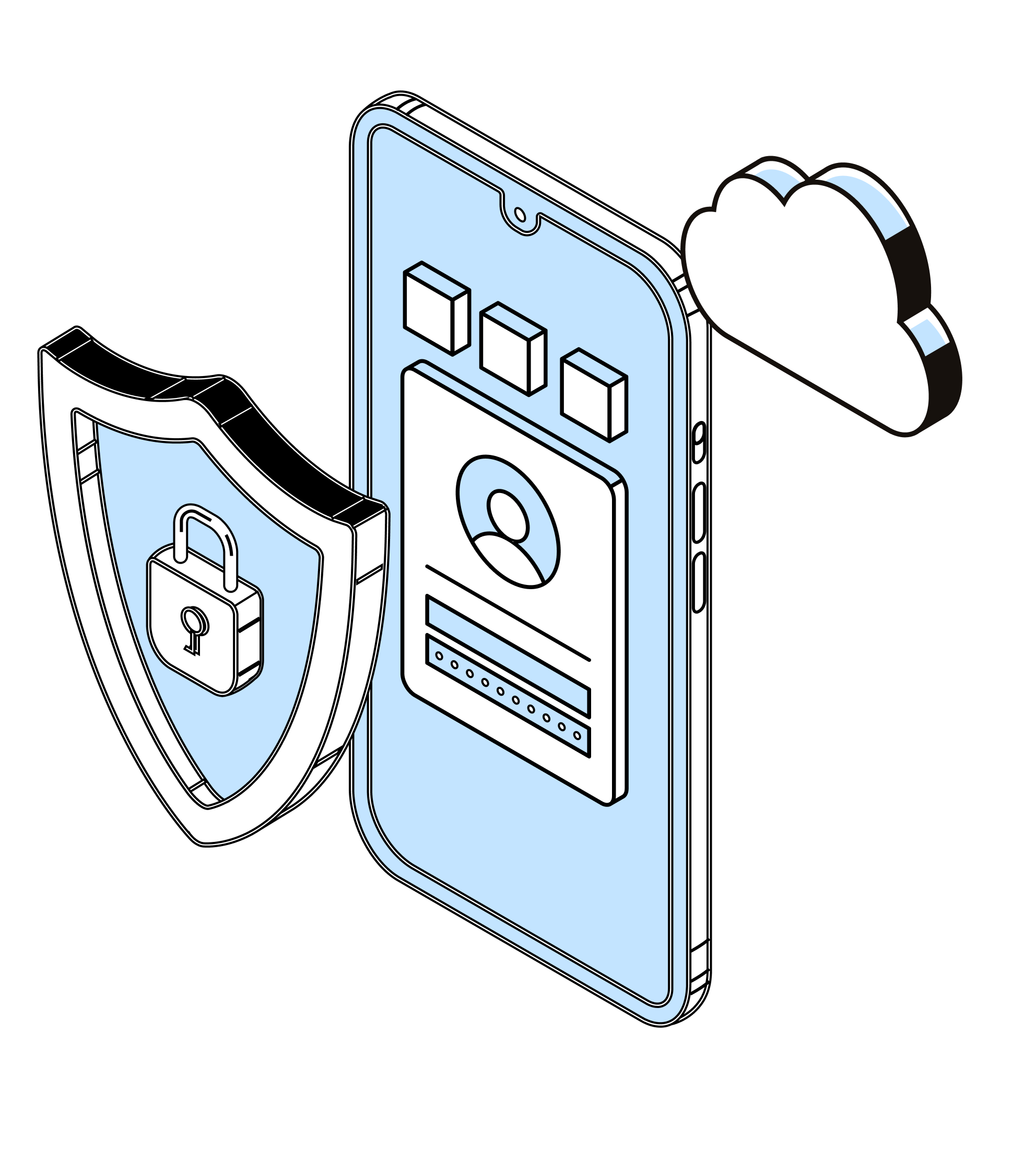
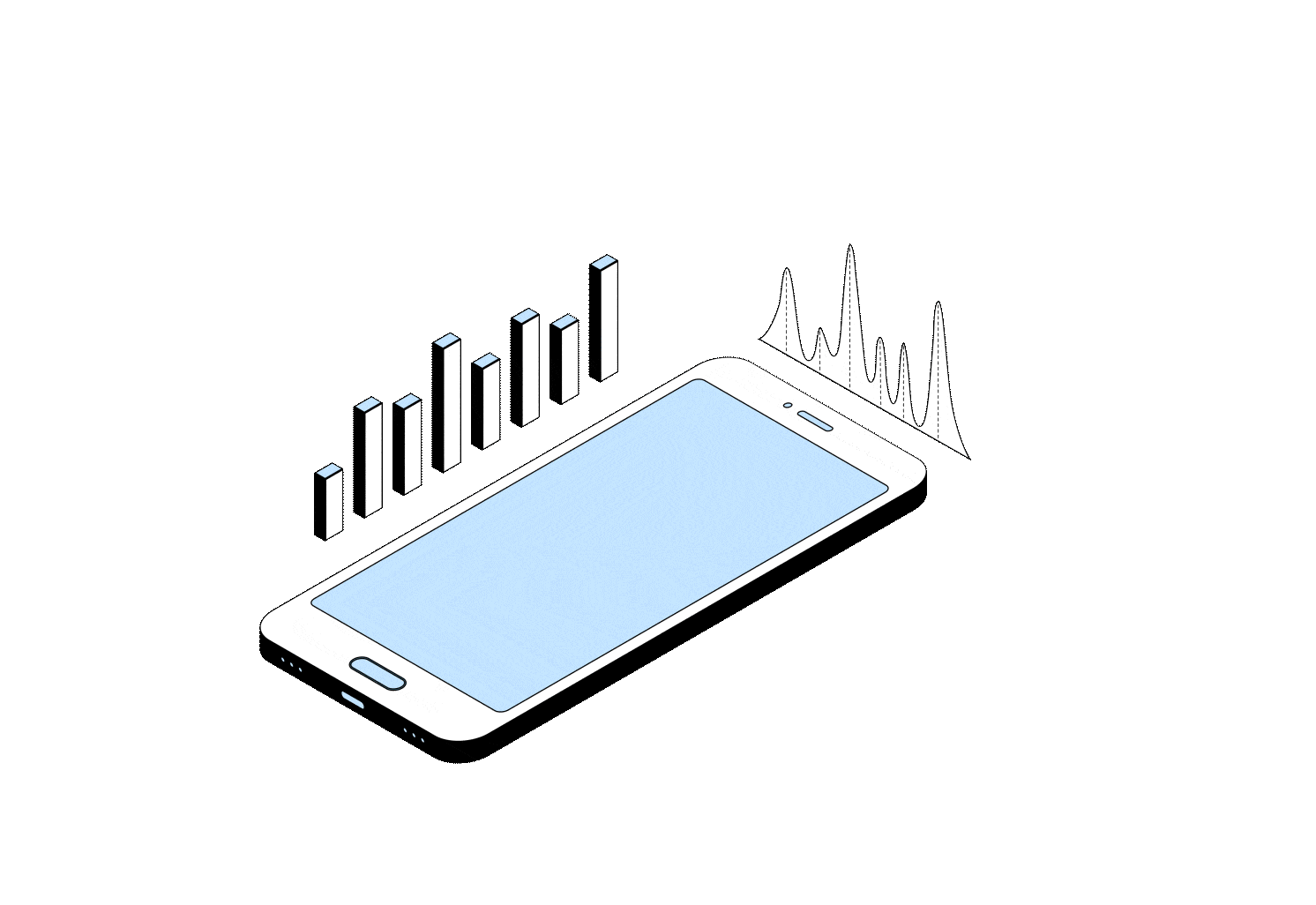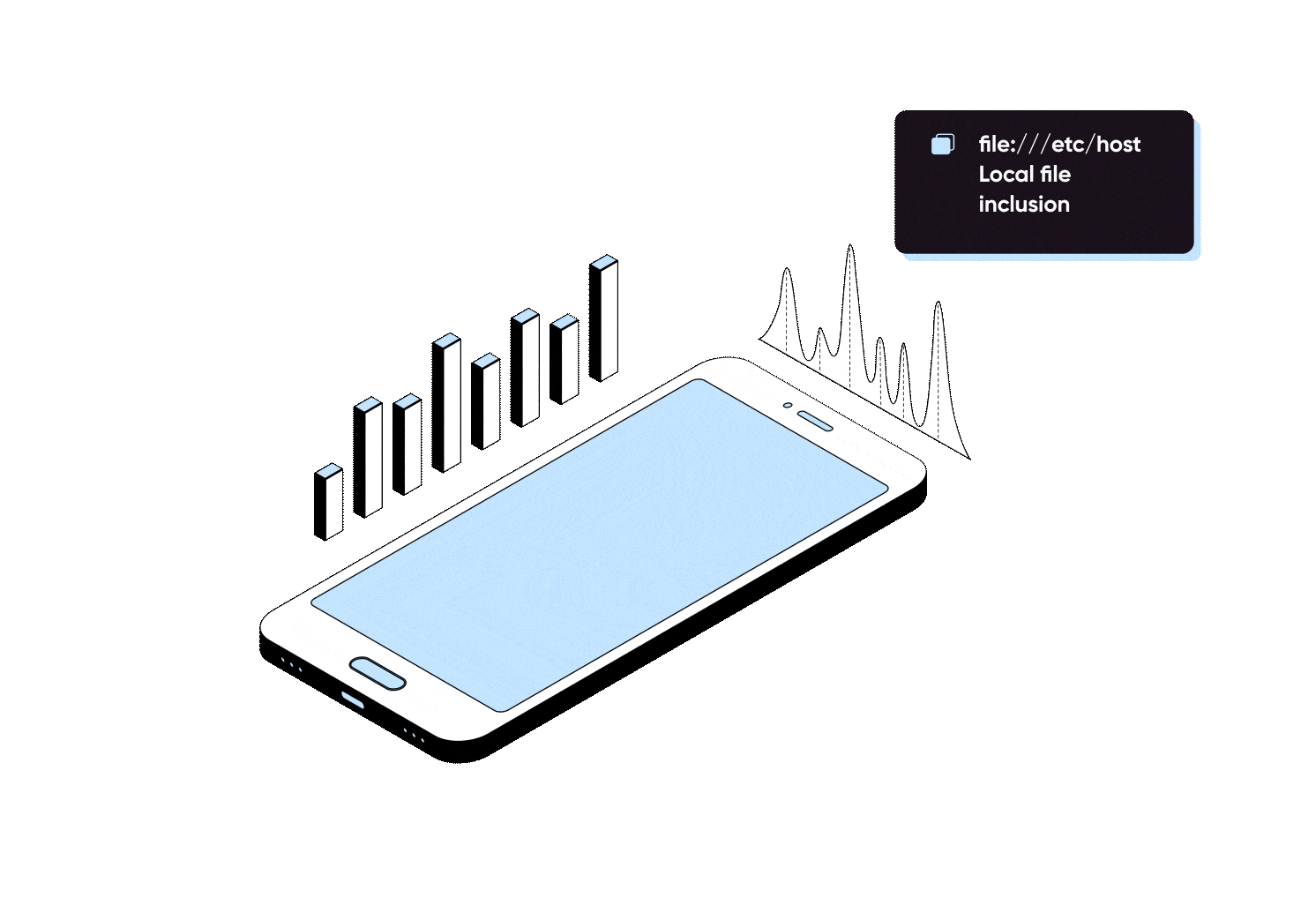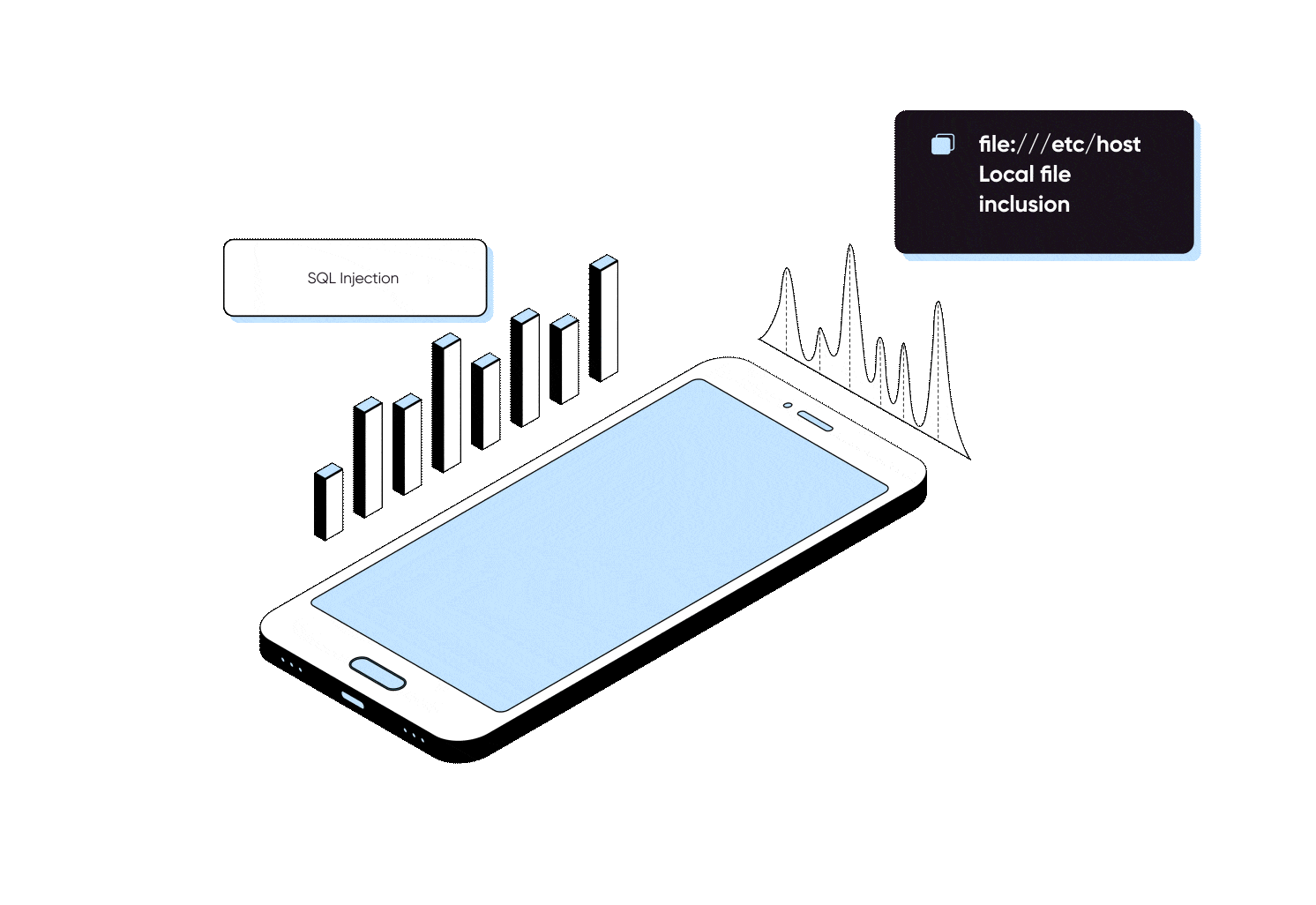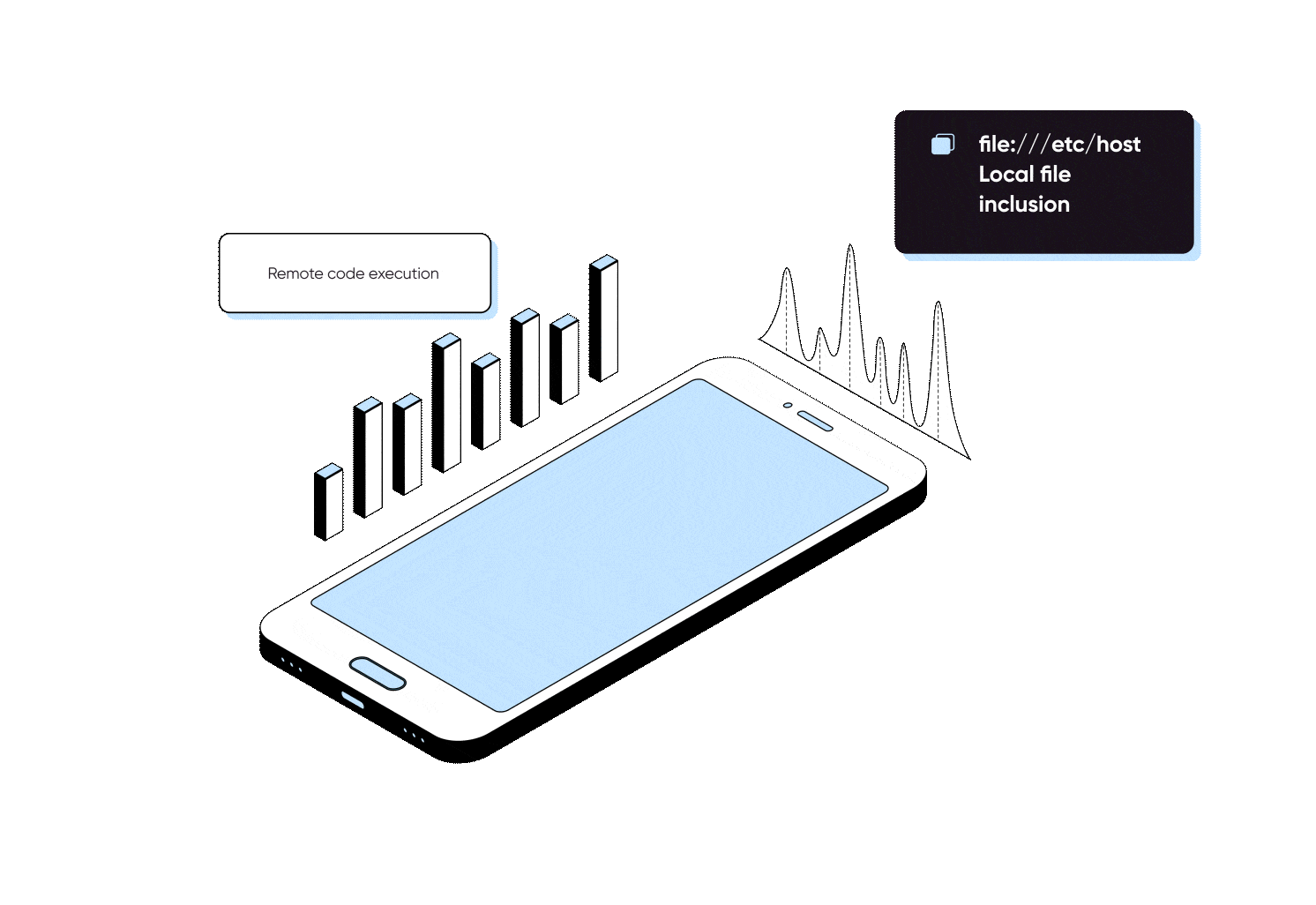
Our extensive, real-world attack scenario-based mobile app penetration testing approach proactively assesses your Android / iOS / Windows based mobile applications for critical vulnerabilities, including client-side and server-side vulnerabilities. By creating custom test cases in line with the OWASP Top 10 Mobile and OWASP Top 10 API frameworks and implementing targeted remediation, our highly skilled bug bounty hunters from Fortune 500 companies like Paypal, LinkedIn, Reddit, and more ensure 360º security of your mobile applications.
Explore our hybrid offensive security modus operandi, which involves a sweeping assessment of your iOS, Windows, and Android mobile applications and APIs to proactively fix critical security gaps before hacker action.
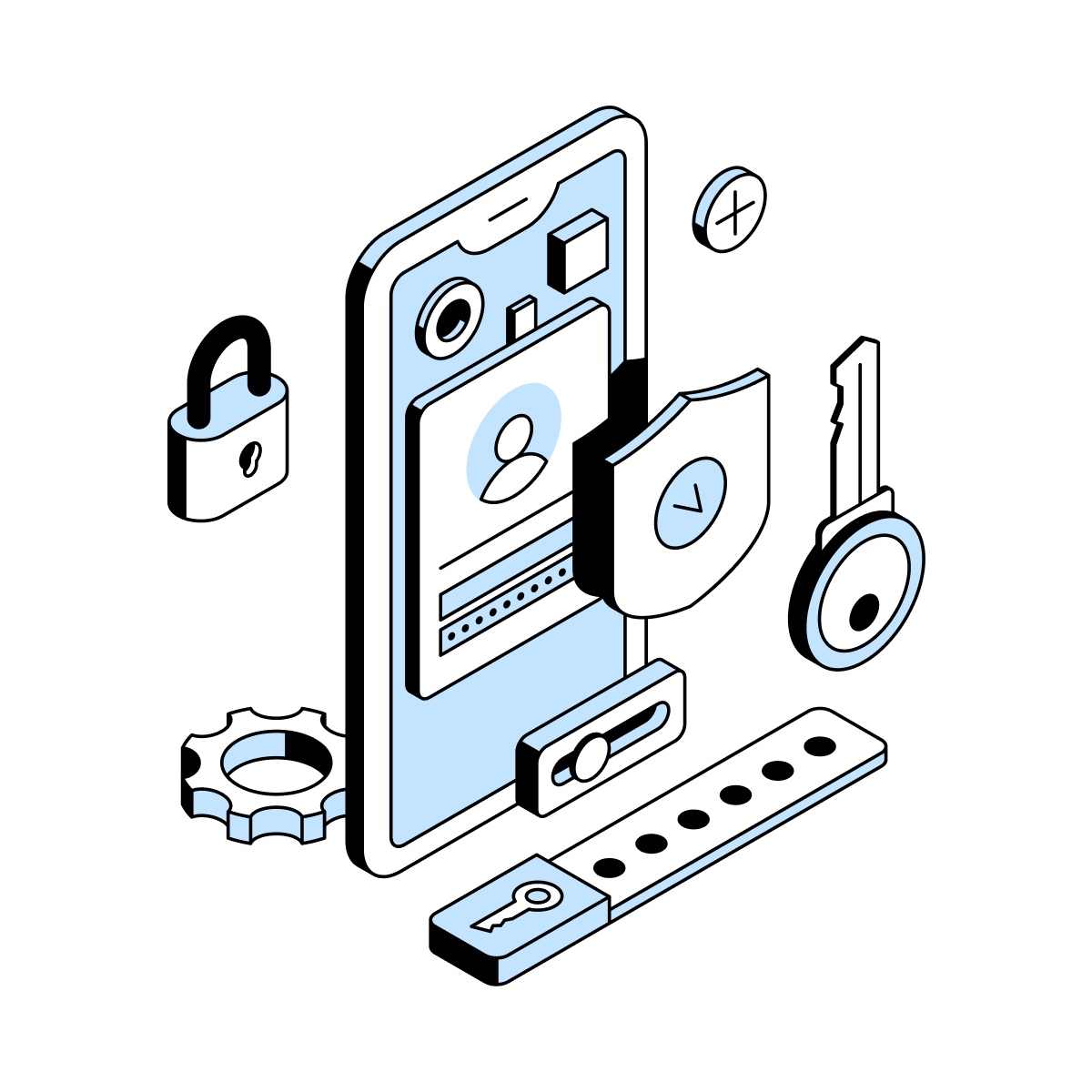



We begin our offensive web app penetration testing with a reconnaissance of your assets and the gathering of exploitable, public information for breaking into user systems.
After reverse engineering, we build unique test cases based on the company’s business and product aligned with the OWASP Top 10 API standards, business logic vulnerabilities, and third-party misconfigurations.
We conduct rigorous client-side and backend API security testing by emulating hacker techniques and tactics to identify hidden security blind spots, ranging from broken authentication, insecure data storage, and security misconfigurations to more traditional issues of server-side injection attacks.
We begin our offensive web app penetration testing with a reconnaissance of your assets and the gathering of exploitable, public information for breaking into user systems.
We begin our offensive web app penetration testing with a reconnaissance of your assets and the gathering of exploitable, public information for breaking into user systems.

Our mobile app penetration testing begins with the reverse engineering of your application and searching for client side vulnerabilities, such as insecure activities, hardcoded sensitive keys and credentials, insecure web views, and more aligned with OWASP top 10 mobile.

After reverse engineering, we build unique test cases based on the company’s business and product aligned with the OWASP Top 10 API standards, business logic vulnerabilities, and third-party misconfigurations.

We conduct rigorous client-side and backend API security testing by emulating hacker techniques and tactics to identify hidden security blind spots, ranging from broken authentication, insecure data storage, and security misconfigurations to more traditional issues of server-side injection attacks.

Based on the exploitation of identified vulnerabilities, we share actionable insights and prescriptive solutions after distilling for all false negatives through our comprehensive reports to ensure your mobile app is hack proof.

We work closely with your Engineering team to implement recommended remediation measures and validate the functioning of the implemented security fixes.
Access accurate and precise reporting of possible security threats and corrective solutions to ensure top-notch app security and a secure SDLC.
Collaborate closely with the top bug hunters from Paypal, LinkedIn, Reddit, and other Fortune 500 companies.
Simulate the hackers’ perspective for vulnerability assessment to discover how security gaps become exploitable, making confidential data insecure, and plug them pre-emptively.
24 x 7 regular support from elite security researchers and professionals for discovering, remediating, and validating security fixes.
Uncover the full spectrum of precarious vulnerabilities in your mobile app’s security architecture and APIs in line with the OWASP Top 10 Mobile and OWASP Top 10 API frameworks.
We have received your request, We’ll get back to you in less than 24hours